I recently came across the sample of Tofsee malware which I find pretty interesting to analysis. I was earlier thinking about putting an write-up about dropper's working and this sample fits perfectly for the situation. The dropper of tofsee is generic and works like most other droppers work.
So, if you are interesting in knowing what droppers do, this article can be useful for you. Also I have tried to put as much as possible details about the analysis procedure, so if you have started your malware analysis journey then you can read this to get an idea about how to proceed the analysis. Definitely you can follow with me but you need to first download the same sample.
Tofsee, When it came in the picture?
Tofsee is not an another new malware family discovered recently in the wild. But it is actually there since few years and has been discovered in 2016. The malware come into spambot categorie and send mostly spam messages, conducting click fraud, mining cryptocurrency. These messages contain malwares as attachment used to deliver to maximum users and create a huge botnet.
The malware consist of a dropper and module(main payload). Dropper is used to drop the module part(main payload) in the system and delete itself. The module connects to various SMTP relays, which it uses to send spam emails. The threat also initiates HTTP connections as it simulates clicking on ads as part of its click fraud mechanism. In next two parts I will analyse the dropper and module will be analysed in future parts probably.
Dynamic Analysis
The sample I am using has following hash:
| Hash | Value |
|---|---|
| MD5: | 57eb38bd35cfa2e65150fa429c1bd9fc |
| SHA-1: | 3e11fcc92127451a38bd82d5cd5b7d4176fbdbba |
The virustotal report shows 34/60 antiviruses has detected it as malicious Full report.
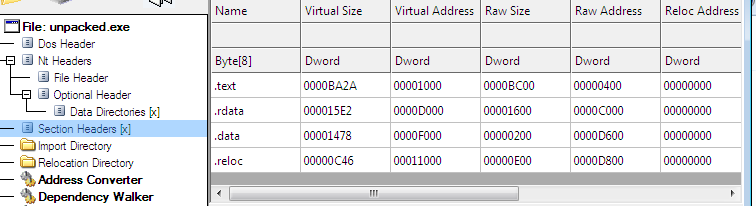
After opening first in CFF Explorer I have notice common section and non obstructed imports present in pe file, which is one hint that no packer is used.
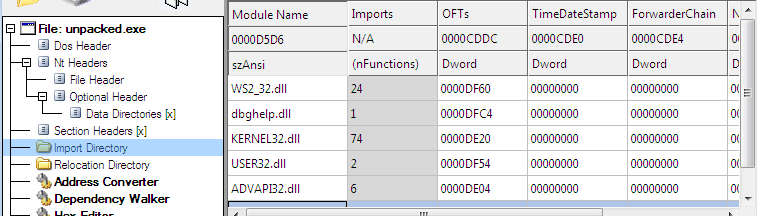
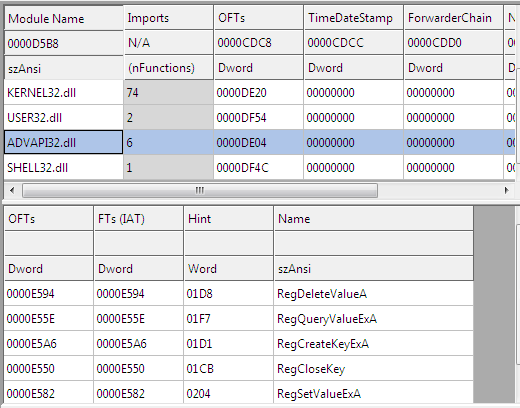
Also from ADVAPI32.dll some registry accessing related functions are used which can give a easy idea that program is doing some registry changes.
Next I loaded the program in DetectitEasy software and look for entropy of different sections.
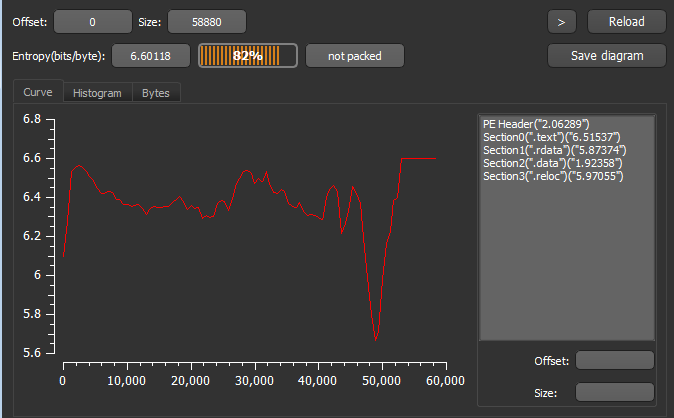
No section has entropy higher then 7, it shows there is less chances that the sections are encrypted or packed.
I opened the program in IDA Pro next. Looking at strings present in program through IDA shows few websites strings and even few ip's. On later analysis I figure out that it is not used by dropper itself but the module that is dumped by dropper use it.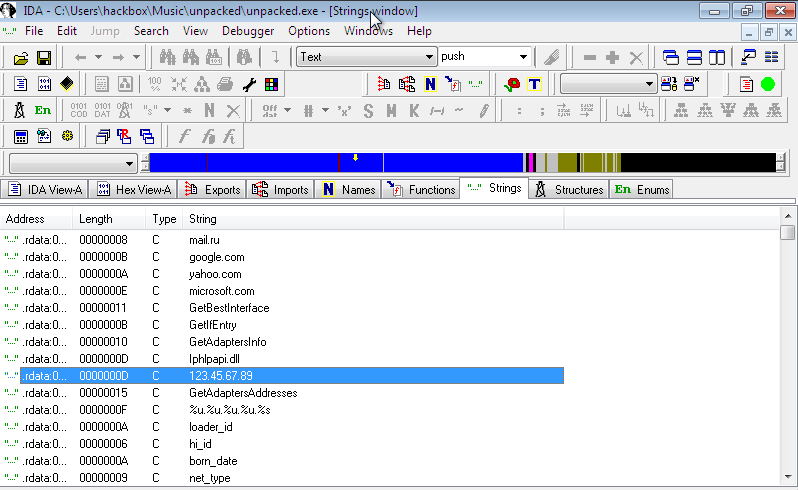
Next I run the program with running Procmon and Process Explorer from sysinternals in background. Process Explorer shows the program runs and started a new service svchost and closed itself.
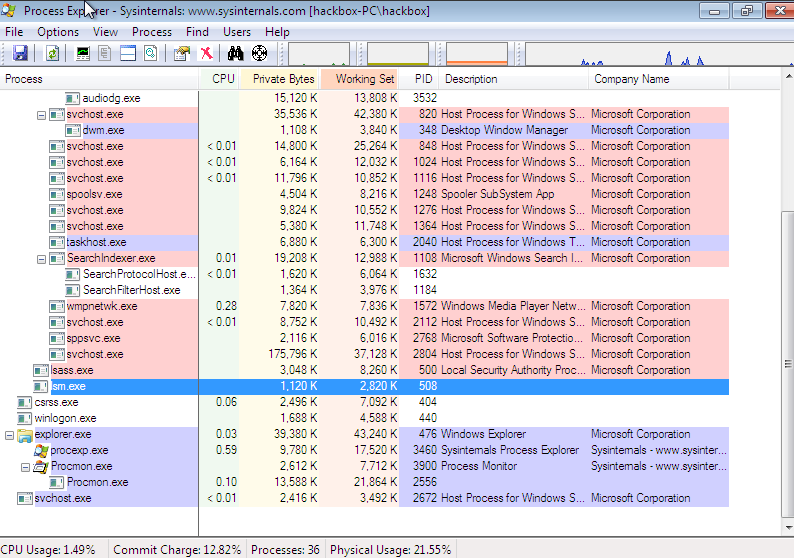 The Last running process with pid 2672 is started by our malicious program before exiting itself.
The Last running process with pid 2672 is started by our malicious program before exiting itself.
The system changes done by program is logged here. It can be seen that the new process started try to connect to some C&C server for some query repeatedly. But since the sample is little old, none of the server actually exists.
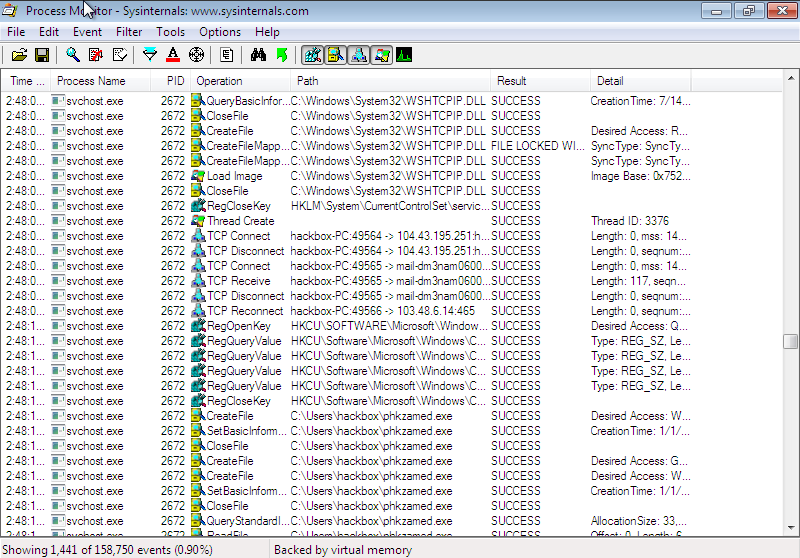
After running the dropper program, the file get deleted afterward to hide itself from user's view.
In the next part we will try to do the static analysis for the dropper sample.








